The best practice approach when it comes to scoping for pci dss is to ensure that everything is covered until approved otherwise.
Pci network segmentation best practices.
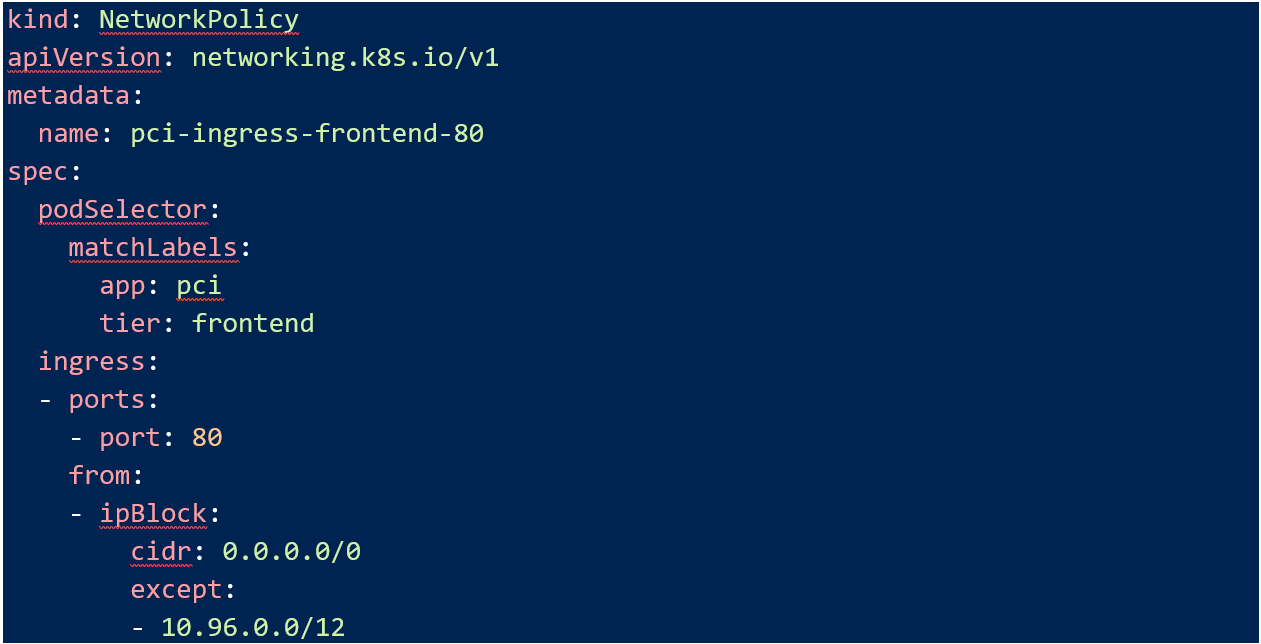
Pci network segmentation is a common approach to reducing the scope and therefore the complexity of card processing networks.
Network segmentation best practices a strong network security structure should contain several parts.
It helps to avoid congestion and bottlenecks in the overall network and separates important segments from other segments.
Remember network segmentation is a best practice not a requirement and the pci dss 1 2 document states that.
For one thing it is essential that your design features an internal zone that is highly protected against breach and never directly accesses the internet.
Network segmentation for pci serves many purposes.
Just as the pci standards make recommendations about how best to keep cardholder data safe they also warn against things you should not do regarding pci data storage.
The framework is composed of the following components.
Network segmentation best practices most businesses have a well defined network structure that includes a secure internal network zone and an external untrusted network zone often with intermediate security zones.
Pci dss payment card industry data security standard and other security standards provide.
Just as with network segmentation there are principles of pci dss and best practices that stipulate who should have access to what data when and under which conditions.
Network segmentation is an approach that when properly implemented can help reduce the number of system components covered by pci dss.
It follows the commonly used strategy of minimization.
When it comes to scoping for pci dss the best practice approach is to start with the assumption that everything is in scope until verified otherwise.
A practical guide to network segmentation table of contents about this guide about network segmentation.
Similar guidance to customers and may have repeatable best practices that they can share with you.
The proposed framework starts by logically breaking up the network infrastructure and placing the business critical resource at the center of the architecture the business critical resource could be anything you want to protect from unauthorized users or objects.
Each organization should follow its segmentation process and procedures according to business requirements.